TLS for Chromium on GNU/Linux
TLS Positive Overrides
Chromium for GNU/Linux can be used with Namecoin for TLS positive overrides; this allows certificates for .bit domains that match the blockchain to be used without errors. Instructions:
- Create a certificate storage directory for ncdns. Make sure that it is only readable and writeable by the user running ncdns.
- Run
echo "$HOME/.pki/nssdb"and note the output; this is your NSS database directory. -
Add the following to your
ncdns.conf. Substitute the certificate storage directory you created above for$CERTDIR, and substitute the NSS database directory that you found above for$NSSDBDIR.[certstore] nss=true nsscertdir="$CERTDIR" nssdbdir="$NSSDBDIR" - Restart ncdns.
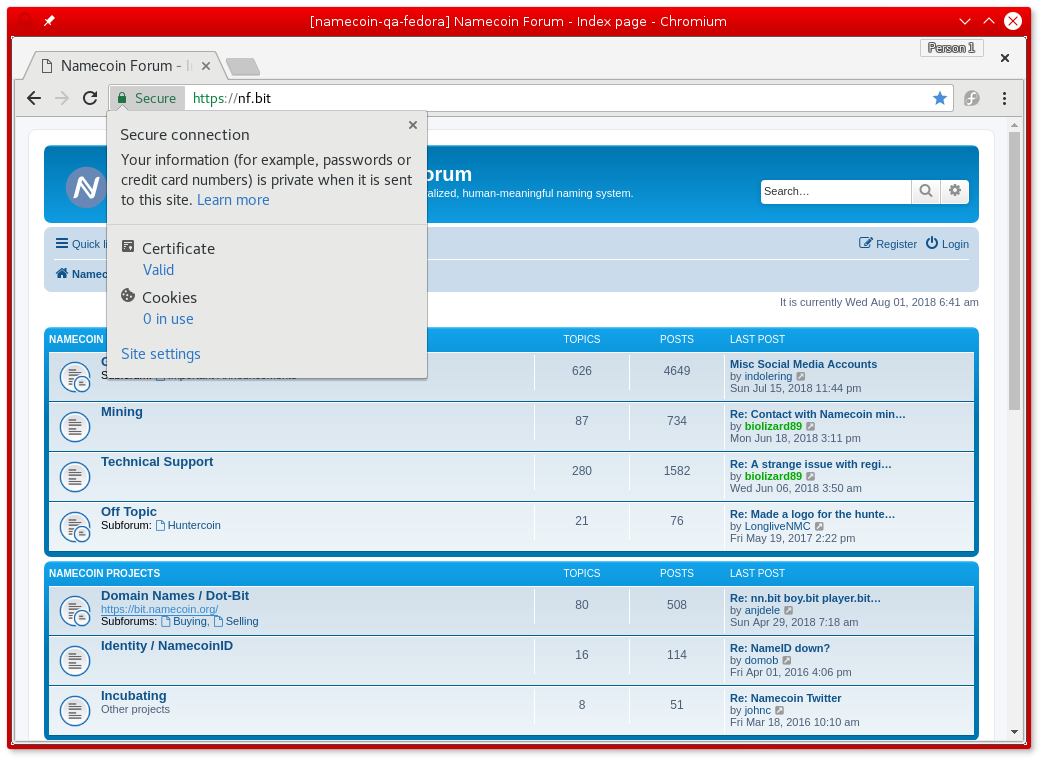
You can now visit in Chromium a .bit website that supports TLS, e.g. the Namecoin forum’s .bit domain. The website should load in Chromium without errors, like in this screenshot:
TLS Negative Overrides (Method A)
Chromium for GNU/Linux can be used with Namecoin for TLS negative overrides; this prevents malicious or compromised public CA’s from issuing certificates for .bit domains. Instructions:
- Exit Chromium.
-
Run the following, and note the output:
ls $HOME/.config/chromium/*/TransportSecurity -
For each
TransportSecurityfile that you found above, run the following, substituting the full path of theTransportSecurityfile for$TS_PATH:./tlsrestrict_chromium_tool --tlsrestrict.chromium-ts-path=$TS_PATH - You can now re-launch Chromium.
TLS Negative Overrides (Method B)
Chromium for GNU/Linux can be used with Namecoin for TLS negative overrides; this prevents malicious or compromised public CA’s from issuing certificates for .bit domains. Instructions:
- Create a temporary directory; make sure that it only is readable/writeable by a user whom you trust with access to the Chromium certificate database. Note its path; make sure you use forward-slashes instead of backslashes, and leave off the trailing slash.
-
Run the following, substituting the temporary directory for
$TEMP_DIR:./tlsrestrict_nss_tool --tlsrestrict.nss-temp-db-dir="$TEMP_DIR" --tlsrestrict.nss-dest-db-dir="$HOME/.pki/nssdb" - Wait a few minutes for
tlsrestrict_nss_toolto finish running.
You’ll need to rerun the above tlsrestrict_nss_tool command whenever the built-in certificate list is updated.
If you’ve manually imported any non-built-in TLS trust anchors to Chromium, and you want to restrict them from intercepting .bit traffic, you should do the following for each such trust anchor:
- Get a DER-encoded certificate of the trust anchor.
-
Run the following, substituing the path to your trust anchor certificate for
$CERT_PATH:./cross_sign_name_constraint_tool --cert.input-root-ca-path="$CERT_PATH" - 3 new certificates will be created:
root.crt,intermediate.crt, andcross-signed.crt. - Delete the existing trust anchor from Chromium.
- Import
root.crtinto Chromium; mark it as a trusted TLS root CA. - Import
intermediate.crtandcross-signed.crtinto Chromium; do not mark them as trusted.
If you decide later that you want to remove the negative overrides from Chromium, follow these instructions:
-
Run the following:
./tlsrestrict_nss_tool --tlsrestrict.nss-temp-db-dir="$TEMP_DIR" --tlsrestrict.nss-dest-db-dir="$HOME/.pki/nssdb" --tlsrestrict.undo -
Wait a few minutes for
tlsrestrict_nss_toolto finish running.
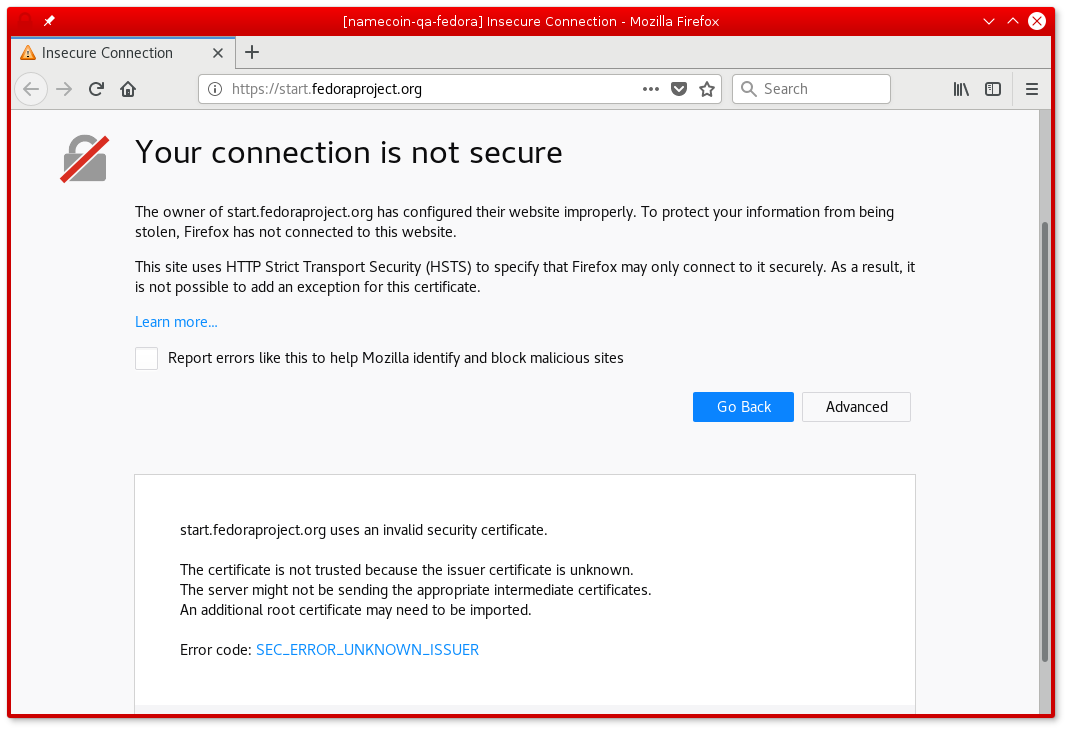
Screenshot
If a .bit HTTPS website uses a CA-signed certificate that doesn’t match the Namecoin blockchain, an error like this will be displayed:
Strict Transport Security
Chromium for GNU/Linux can be used with Namecoin for Strict Transport Security; this improves security against sslstrip-style attacks by forcing HTTPS to be used for .bit domains that support HTTPS. Instructions:
- Install ncdns.
- Download and extract certdehydrate-dane-rest-api from the Beta Downloads page.
-
Create a text file called
certdehydrate_dane_rest_api.confin the same directory wherecertdehydrate-dane-rest-apiis, and fill it with the following contents (if ncdns is listening on a different IP or port, change the following accordingly):[certdehydrate-dane-rest-api] nameserver="127.0.0.1" port="5391" - Run
certdehydrate-dane-rest-api. - If you want to test certdehydrate-dane-rest-api, try visiting
http://127.0.0.1:8080/lookup?domain=ca-test.bitin a web browser. You should see a certificate. If you instead get an error or an empty page, something is wrong. - Download the DNSSEC-HSTS WebExtensions Component from the Beta Downloads page.
-
Install the DNSSEC-HSTS WebExtensions Component like this:
unzip -d ./dnssec-hsts ./dnssec-hsts-*.xpi sudo rm -rf /usr/share/webext/dnssec-hsts/ sudo cp -a ./dnssec-hsts /usr/share/webext/dnssec-hsts sudo ln -s -T /usr/share/webext/dnssec-hsts "/usr/share/chromium/extensions/dnssec-hsts"
You may need to restart Chromium.
.bit domains that support HTTPS will now automatically redirect from HTTP to HTTPS in Chromium.